Scale Cloud Security Efficiently
Block cloud misconfigurations and rapidly remediate Infrastructure as Code (IaC) risks with actionable insights and proactive protection
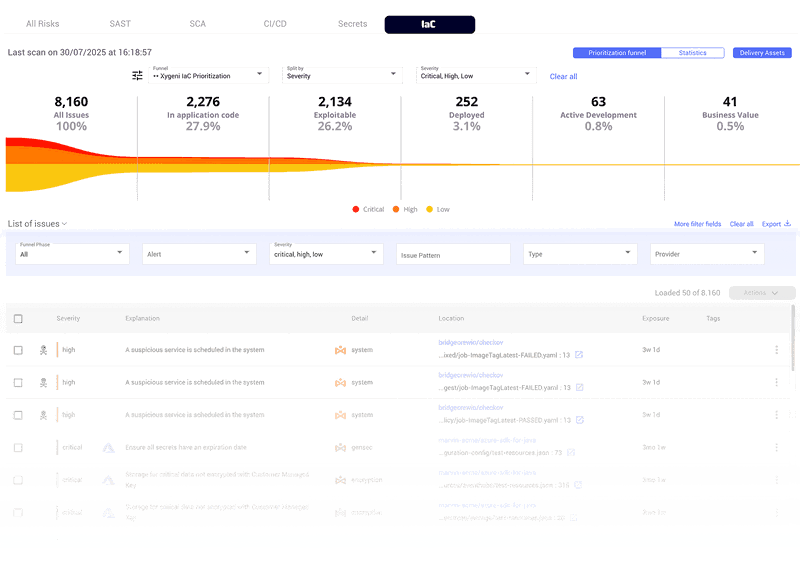
Identify All Cloud Misconfigurations
Detect critical alerts for your cloud across various misconfiguration types, such as unsecured access, unencrypted keys, and more without effort.
Simplify Your Prioritization Process
Reduce the time needed to triage and remediate IaC risks by identifying the most significant ones and providing detailed remediation guidelines.
Block Risks In Every Step
Integrate proactive IaC security directly into CI/CD workflows, alerting developers and halting processes upon any misconfiguration or policy violation.
Xygeni IaC Security's Capabilities and Functionalities
Adapt Scanning to Any Environment
Scan private and public registries, local file systems, and various container formats, including tar archives, Podman, and Git repositories, supporting diverse execution environments.

Secure Your Cloud Without Effort
Deploy extensive predefined policies to address major cloud security challenges such as infrastructure misconfigurations, container vulnerabilities, and exposed secrets.
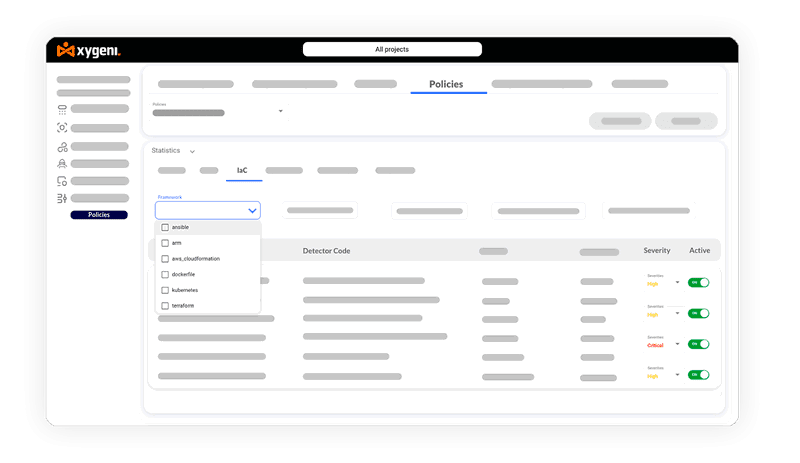
Gain Insightful Context-Driven Feedback
Connect IaC vulnerabilities with infrastructure and application flaws, considering their context to ensure developers focus only on the critical risks.
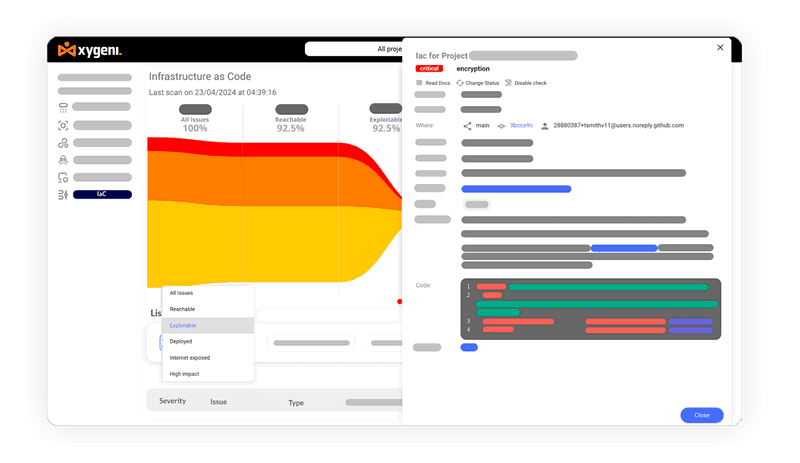
Block IaC Misconfigurations Before Production
Integrate IaC scans with security best practices and guardrails in development workflows to avoid noisy redundant and overwhelming alerts.
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved