Cut Noise. Fix Fast. Deliver Secure.
One platform that protects your SDLC end-to-end without moving your code off your infrastructure.
SAST - Code Security
Xygeni SAST with AI
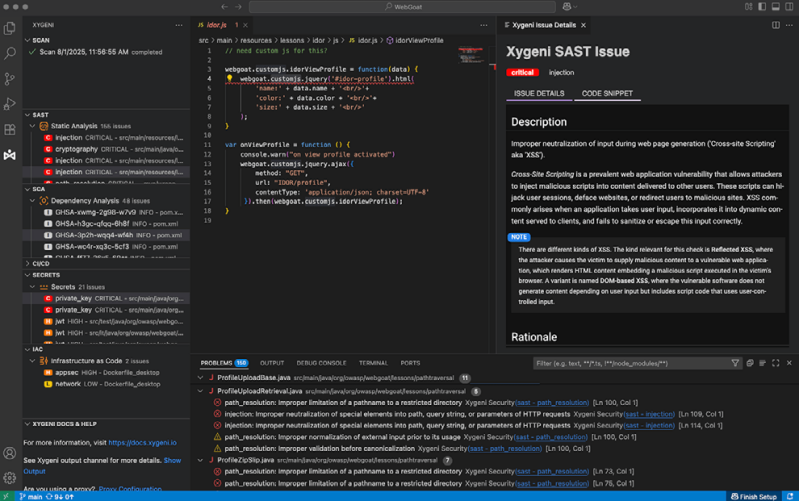
Modern applications face risks from both external attacks and insider threats.Vulnerabilities in proprietary code and injected malware can cause severe damage,from data breaches to operational failures and reputational loss.
Xygeni Al SAST combines advanced static analysis with intelligent malware detection to deliver unmatched protection for proprietary code.It identifes injection flaws,misconfigurations,and hidden threats such as backdoors or logic bombs before they reach production.
Al AutoFix applies secure.context-aware fixes directly in pull requests,helping developers remediate issues instantly without slowing down delivery.High-speed scans and IDE integration keep teams productive while maintaining security at every stage.
A risk-based prioritization engine filters findings by exploitability and impact,cutting noise and focusing attention on what truly matters.With exceptional accuracy and automation,Xygeni empowers DevSecOps teams to build and ship secure software faster.
SCA - Open Source Security
Real-time security for open-source dependencies
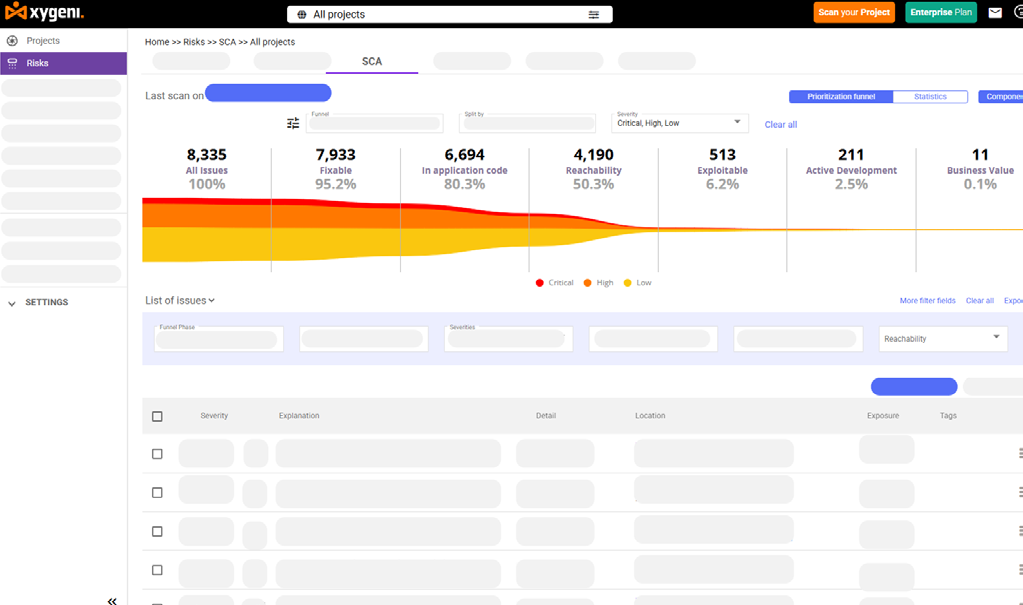
Identify all direct and transitive dependencies and benefit from real-time malware detection, blocking,and notification with early alerts and expert verification.
Prioritize SCA findings by going beyond CVSS scores and incorporating contextual factors such as reachability.business impact,and technical relevance,saving time for both security and development teams.
Evaluate Remediation Risk to choose the safest fix and prevent breaking changes before updating dependencies.
Automatically upgrade to vulnerability-free open-source dependencies through automated pull requests or manual prompts,ensuring efficient and consistent dependency management.
Export up-to-date SBOMs in CycloneDX and SPDX formats to streamline the sharing of vulnerability and license information across projects and partners.
CI/CD Security
Improve Visibility and Security in your Cl/CD Pipelines and Tools
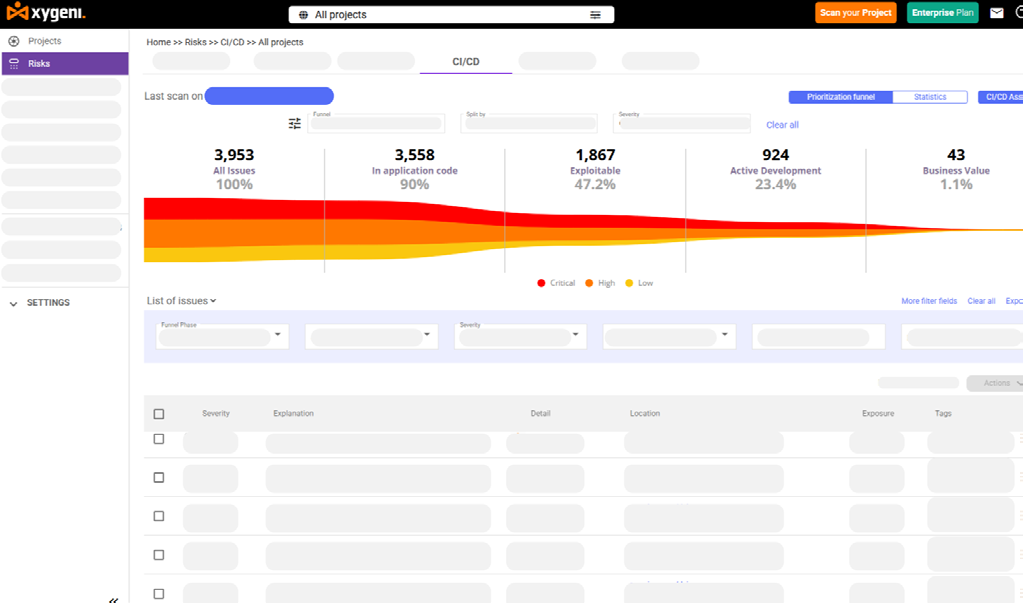
Continuously scan your pipelines executions to block supply chain attacks and maintain oversight of CI/CD security policies,configurations,and governance.
ldentify misconfigurations in tools,configuration files, build scripts,and Cl/CD pipelines and enforce least privilege policies to prevent unauthorized access or compromise code.
Ensure compliance with standards such as ClS,NIST, OpenSSF,or any other software supply chain framework by governing security policies specifc to each product or pipeline.
Secrets Security
Block Secrets Leakage at All Stages of Development
Robust defense against secret leakage within the software development lifecycle.Our advanced solution scans,detects,and blocks the publication of sensitive information such as passwords,APl keys,and tokens in real-time.
Focus on the most critical risks and automatically remediate them with customized playbooks, and actionable guidance.
Identify secrets in any file,pipeline,container and repositories.Analyze Git history to detect new or removed secrets.Remove false positives and alert fatigue through intelligent validation of secret status.
Immediate defense by halting commits through integration with Git hooks.Customisable detectors for patterns and locations for a unique business alignment.
IaC Security
Secure Your Infrastructure Automation with Precision

Maximize the reliability and security of your infrastructure as code processes.Our advanced laC solution ensures that your automated configurations are not only efficient but protected against vulnerabilities from development to deployment.
Detect hundreds of cloud misconfigurations with predefined policies that address the most common cloud security challenges.
Connect lac vulnerabilities with infrastructure and application flaws to focus on the most critical risks.
Implement guardrails in development workflows to block misconfigurations before they reach production.
Build Security
Secure Your Build Process from Code to Deployment
Ensure continuous integrity,artifact verification and attestation across your build process to prevent tampering without disrupting development.Seamlessly add attestation to your pipelines and verify all software materials. blocking any tampered artifacts before delivery or deployment.
Real-Time Artifact Verification confirms build integrity,supporting storage in any registry and enhancing security with simple,keyless signatures.
Supports SLSA Provenance and custom in-toto attestations,providing detailed insights and multiple predicates like vulnerability scans,SBOM formats,and test results for comprehensive build visibility.
Anomaly Detection
Real-Time Protection Against Exploits in Your Software Supply Chain
Supply Chain Real-time analytics to synchronize event analysis and change monitoring,quickly detecting and blocking suspicious actions in the Cl/CD infrastructure and processes.
Block tampering in your codebase, pipelines, configuration and other critical files for your organisation.Provide detailed insights and context information to improve response efficiency.
Customizable rules to ensure relevant alerts for the organisation.Immediate alerts for suspicious behaviour through email or your preferred messaging platform.
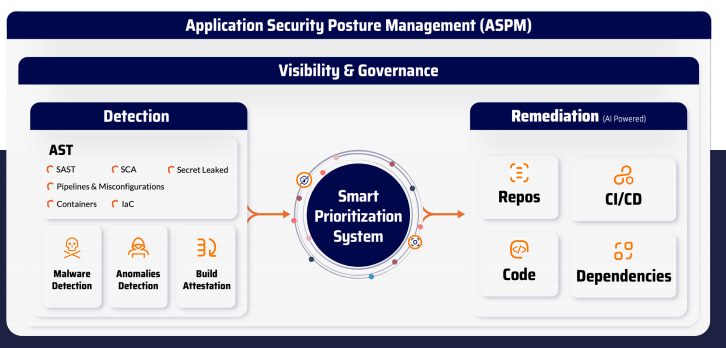
ASPM
Unifying Risk Management from Code to Cloud
Xygeni's Application Security Posture Management (ASPM)enhances your team's ability to visualize, prioritize,and remediate risks with ease.Our platform offers real-time visibility and contextual insights. ensuring robust protection for your applications from development to deployment.
Automatically discover,catalog,and assess all software assets across repositories,pipelines,and cloud environments to gain a unified view of risks prioritized by business impact.
Ingest findings from the third-party tools like SAST.SCA.and laC scanners,consolidating them into a single dashboard to streamline vulnerability management.
Use Dynamic Funnels to refine prioritization by exploitability. reachability.and other contextual factors,focusing on what truly matters.
Xygeni Security Platform
Xygeni is a cloud-native platform that helps mid to large organizations protect their software releases from malicious attacks and vulnerabilities. Thus, these companies deliver secure and reliable applications by reducing the attack surface of their software supply chain.
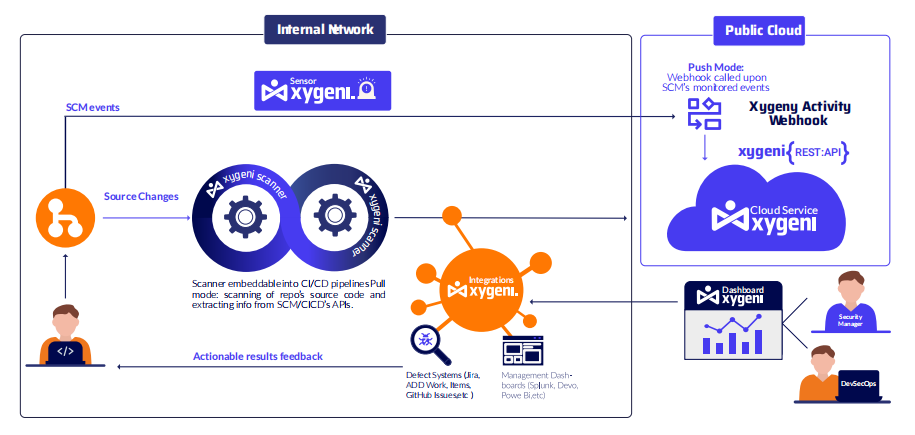
Xygeni Scanner
Run via a command-line interface(CLI)or integrated into several parts of the Development Workflow according to the corporate preferences and needs.It runs analysis commands separately or simultaneously for specific tasks,such as detecting hard-coded secrets or Cl/CD misconfigurations. This approach ensures that your code never leaves your organization's ecosystem.
Xygeni Integrations
Xygeni provides out-of-the-box integrations with several SDLC systems to enable continuous monitoring through every step in the SDLC.
Xygeni Sensor
Xygeni monitors activity on code repositories and other tools to detect potential attacks,such as deactivating security measures,attempting to execute risky actions or skipping corporate security policies.As a result,customers of Xygeni receive alerts when a security issue may impact them.
Xygeni Web Ul
Browser-based with many functions such as configuration settings,access to the security posture of the organization and each project and asset,trends exploration,reporting,and other facilities.
Xygeni Bot
The Xygeni Bot runs remediation tasks on-demand,on pull requests,or daily.It creates smart PRs with ready to-merge fixes,closing the loop between detection and remediation.
Secure your Software from Code to Cloud
Detect vulnerabilities,block malware,prevent misconfigurations,and protect your entire software supply chain, all in one powerful platform.
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved