
Is your web application safe?
I would like to say, "My network application has a firewall, and intrusion detection system, of course, very safe!" But do you know the following information?
1. Hackers are mainly concerned with the application of the site: shopping cart and login interface
2. Web applications are usually customizable, so less tested
3. Firewall / network-level defense is basically not much protection
See here, you will be confident that their network application is safe?
Well, if you also "mouth", then look at the following news:
1. On April 17, 2011, BarracudaNetworks suffered a SQL injection attack with a network application firewall installed
2. On March 27, 2011, MySQL.com suffered a SQL injection attack
3. On July 4, 2010, YouTube was hacked by the cross-site scripting (XSS) vulnerability
4.On February 6, 2010, Kaspersky was attacked by SQL

Since the network application there are many security risks, choose what kind of vulnerability scanning tool?
Internet security experts tell you: of course, Acunetix vulnerability scanning software! Because it has:
1. Industry leading crawler
Detects custom 404
You can skip the login section and log in on the logger
Can handle the verification code format
Supports single sign-on and security token mechanisms
Understand the scope of the page, according to different circumstances to take different measures
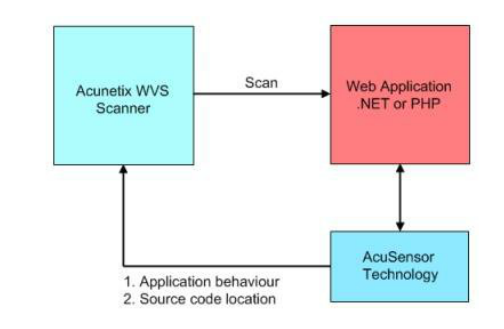
2. Acunetix AcuSensor technology
Combine black box scanning with source code analysis
Analyze the code that has been executed
Detect more vulnerabilities
Less false positives, time savings for security personnel and developers: advanced technologies including verifying vulnerabilities; analysis of feedback and fine-tuning attacks; analysis of software behavior during operation
A configuration problem or runtime environment is found in the web server
3. Advanced SQL injection attacks
First-class SQL injection attack detection
Network security experts agree that Acunetix can see more SQL injection vulnerabilities than other vulnerability scanning software
Can be used for SQL blind detection
AcuSensor technology verifies all SQL reports, including SQL embedding
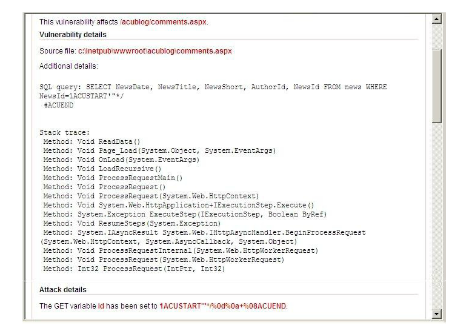
Report SQL injection vulnerabilities for SQL injection attacks, POST variables, and stack traces
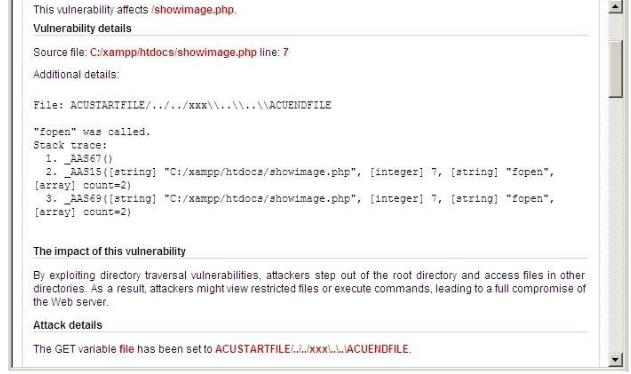
Indicates the location of the password vulnerability
4. High-end cross-site script
Discover more cross-site scripting vulnerabilities (XSS)
Analyze whether the character is encoded or filtered
Based on application feedback analysis results
Use a heuristic method based on hacking methods
Unlike other scanners that send requests and then ignore them
5. User-friendly interface: all tools are integrated in a simple and intuitive graphical user interface

6. The configuration is simple, easy to debug
Custom 404 detection
Using custom detection techniques (PHP, ASP, etc.)
Click the configuration configuration for the certified zone
Manual scan page submitted to the scanner for analysis
7. Advanced penetration testing tools
HTTP editor
HTTP network sniffer
HTTP Scanner
Authentication tester
8. Provide specific loopholes to repair recommendations
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved