N-Stalker Web Application Security Scanner X is a sophisticated Web Security Assessment solution for your web applications. By incorporating the well-known “N-Stealth HTTP Security Scanner” and its 39,000 Web Attack Signature database along with a patent-pending Component-oriented Web Application Security Assessment technology, N-Stalker is a “must have” security tool to developers, system/security administrators, IT auditors and staff.
What is N-Stalker?
N-Stalker Web Application Security Scanner X is a sophisticated Web Security Assessment solution for your web applications. By incorporating the well-known “N-Stealth HTTP Security Scanner” and its 39,000 Web Attack Signature database along with a patent-pending Component-oriented Web Application Security Assessment technology, N-Stalker is a “must have” security tool to developers, system/security administrators, IT auditors and staff.
How N-Stalker will help me?
If you are concerned about SQL injection and Cross-site scripting attacks, N-Stalker will sweep your Web Application for a large number of vulnerabilities, including well-known standards such as “OWASP Top 10” and “PCI Data Security”, and also custom security inspections to ensure your application’s Secure Development Life Cycle (SDLC).
What’s new in N-Stalker X
Parallel Spider Engine
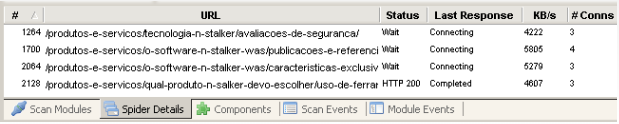
N-Stalker debuts a new spider engine to allow simultaneous fetching of web resources. This new feature provides a more effective way to traverse your application and search for web interfaces. If you want to inspect multiple requests, just press “Track Spider” and follow N-Stalker’s HTTP activities on demand.
Improved Attack Engine
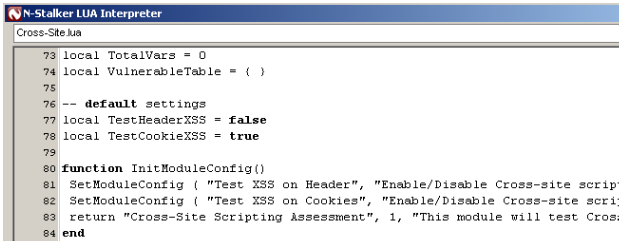
N-Stalker X attack modules are based on a customized engine running LUA language. It provides a flexible integration and allow for a fast introduction of new attack patterns. From OWASP Top 10 to CWE Top 25, N-Stalker X provides way to integrate your own signatures into his own inspection engine.
Enhanced Web Engine
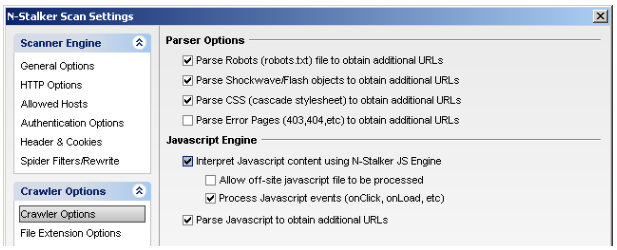
Based on open-source engine, N-Stalker X supports all kind of modern technologies such as HTML5, Flash/Flex and Javascript language, including full support for asynchronous requests (Ajax experience). N-Stalker will interpret scripts and integrates your HTML’s DOM (Document Object Model) just like if a human-guided web browser was navigating through your application. Proprietary objects such as Shockwave/Flash applications will be easily processed allowing for a transparent crawling process.
Integrated Web Proxy for “drive-thru” attacks

An integrated web proxy in N-Stalker’s spider engine to allow for a drive-thru navigation and security testing for restricted and well-defined scopes. Just open your favorite browser, run your test cases and record well-known application transactions that can be used for an extended security assessment.
Support for Manual Security Analysis
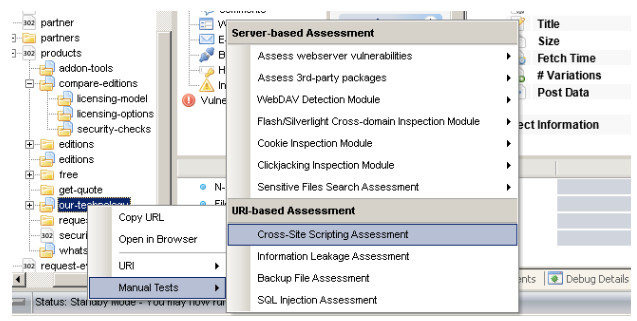
N-Stalker Security Checks
| 》Web Engine N-Stalker |
ENTERPRISE |
INFRA |
| Web Spider Module |
 |
 |
| 》Custom Design Errors |
ENTERPRISE |
INFRA |
| Cross-site Script Injection Module |
 |
 |
| Database Tampering – SQL Injection Module, including: |
 |
 |
| – Direct mode |
 |
 |
| – Blind mode |
 |
 |
| Buffer & Integer Overflow attack Module |
 |
 |
| Format String attack Module |
 |
 |
| File & Directories Tampering Module, including: |
 |
 |
| – Backup Files Discovery |
 |
 |
| – Configuration Files Discovery |
 |
 |
| – Password Files Discovery |
 |
 |
| – Information Leakage Discovery |
 |
 |
| Parameter Tampering Module, including: |
 |
 |
| – Special Parameter Addition attacks |
 |
 |
| – Boolean Parameter Tampering attacks |
 |
 |
| – Hidden Parameter Discovery |
 |
 |
| – Parameter Deletion attacks |
 |
 |
| – Remote Execution attacks |
 |
 |
| – File & Directory traversal attacks |
 |
 |
| – Header Splitting & CRLF Injection attacks |
 |
 |
| – Remote File Include PHP-based attacks |
 |
 |
| Check for Suspicious Values in Web Form Hidden Fields |
 |
 |
| Custom Signature Check (via Signature Editor) |
 |
 |
| 》Web Server Exposure |
ENTERPRISE |
INFRA |
| Web Server Infrastructure Analysis Module, including: |
 |
 |
| – Web Server & Platform version vulnerabilities |
 |
 |
| – SSL encryption and X.509 certificate vulnerabilities |
 |
 |
| – HTTP Method Discovery Module |
 |
 |
| – HTTP Fingerprint Module, including: |
 |
 |
| – Web Server Fingerprint Module |
 |
 |
| – Web Server technology Discovery Module |
 |
 |
| – Directory Brute-Force |
 |
 |
| – HTTP Protocol vulnerabilities |
 |
 |
| 》Web Signature Attacks |
ENTERPRISE |
INFRA |
| Web Attack Signatures Module, including: |
 |
 |
| – IIS CGI Decode Test |
 |
 |
| – IIS Extended Unicode Test |
 |
 |
| – IIS File Parsing Test |
 |
 |
| – FrontPage Security Test |
 |
 |
| – Lotus Domino Security Test |
 |
 |
| – General CGI Security Test |
 |
 |
| – HTTP Devices Security Test (routers, switches) |
 |
 |
| – Windows-based CGI Security Test |
 |
 |
| – Windows-based CGI Security Test |
 |
 |
| – PHP Web Application Security Test |
 |
 |
| – ASP Web Application Security Test |
 |
 |
| – J2EE Web Application Security Test |
 |
 |
| – Coldfusion Web Application Security Test |
 |
 |
| Attack templates such as: |
 |
 |
| – Complete, SANS/FBI Top10, Top20 |
 |
 |
| 》Confidentiality Exposure Checks |
ENTERPRISE |
INFRA |
| Look for Web forms vulnerabilities, including: |
 |
 |
| – Password cache feature |
 |
 |
| – Insecure method for sending data |
 |
 |
| – Lack of Encryption for sensitive data |
 |
 |
| – Insecure location to send data (leakage) |
 |
 |
| – Find directory listing |
 |
 |
| – Find available objects to download |
 |
 |
| – Find meta-tag leakage |
 |
 |
| – Find sensitive keywords in comments and scripts |
 |
 |
| Compliance analysis, including: |
 |
 |
| – Find Copyright statements |
 |
 |
| – Find content rating statements |
 |
 |
| – Find custom content on web pages and forms |
 |
 |
| 》Cookie Exposure Checks |
ENTERPRISE |
INFRA |
| Cookie Security Analysis Module, including: |
 |
 |
| – Find weakness in cookie information |
 |
 |
| – Find cookies sent without encryption |
 |
 |
| – Find information leakage in cookie information |
 |
 |
| – Find cookies vulnerable to malicious client-side script |
 |
 |
| 》File & Directory Exposure Checks |
ENTERPRISE |
INFRA |
| Search for backup files |
 |
 |
| Search for information leakage files |
 |
 |
| Search for configuration files |
 |
 |
| Search for password files |
 |
 |


















































































































































