Known Exploited Vulnerabilities (KEVs) are CVE-listed vulnerabilities confirmed to be exploited in the wild. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) maintains the official KEV Catalog and mandates remediation timelines through Binding Operational Directive 22-01. Many private organizations now use this list to prioritize patching.
Although CVSS scores measure potential impact, KEVs represent active exploitation. In other words, they turn “maybe exploitable” into “being exploited,” requiring faster SLAs and automated guardrails.
KEVs vs CVEs vs EPSS
Security teams often confuse these related terms. Understanding the difference is crucial for accurate risk
|
Acronym |
Source |
Purpose |
|
CVE |
NVD |
Unique identifier for a disclosed vulnerability. |
|
CVSS |
NVD / FIRST |
Measures theoretical severity (impact + exploitability). |
|
EPSS |
FIRST.org |
Predicts probability of exploitation within 30 days. |
|
KEV |
CISA |
Confirms real-world exploitation and sets patch deadlines. |
Together, these systems form a hierarchy of risk: CVSS shows how bad it could be, EPSS shows how likely it is, and Known Exploited Vulnerabilities show what’s actually happening.
Why KEVs Matter for Developers and CISOs
Firstly, KEVs highlight live attacker behavior. Secondly, they frequently involve third-party components, frameworks, containers, or CI/CD dependencies, that teams assume are safe. Consequently, a delayed fix can open lateral-movement paths inside your build and delivery infrastructure.
Recent examples:
Takeaway: KEVs are not potential threats, they’re active ones. Therefore, treat every Known Exploited Vulnerabilities as “fix-now”, unless reachability analysis proves otherwise.
How to Track and Prioritize Known Exploited Vulnerabilities
To begin with, check the official CISA Known Exploited Vulnerabilities Catalog and mark any matches inside your security scanner. Then, use this information to decide which fixes need to happen first. In addition, combine Known Exploited Vulnerabilities with EPSS scores to cut noise and focus on the weaknesses that really affect your running code.
Step-by-step workflow:
·Internet-facing vulnerabilities: fix within 1–3 days.
·Internal ones: fix within a week.
·Code not in use: keep an eye on it and verify often.
From Awareness to Action: Automating Fixes with Xygeni
In practice, handling all this by hand doesn’t scale. Therefore, Xygeni connects Known Exploited Vulnerabilities directly to your CI/CD workflows, turning alerts into real, guided actions.
In short, threat intelligence shows what’s being attacked, Xygeni ensures it gets fixed quickly, safely, and automatically.
Example Guardrail Policy (YAML)
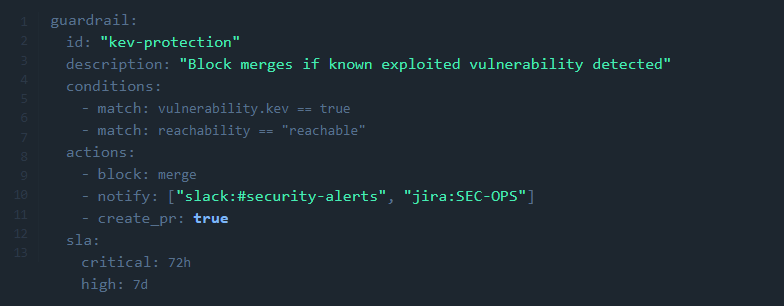
This rule enforces no merge for active Known Exploited Vulnerabilities, notifies relevant channels, and auto-creates a fix PR, all within your CI/CD guardrails.
Mini Case: Preventing a KEV Deployment
Outcome: The team avoided shipping a known exploited vulnerability to production and resto red pipeline flow within the same sprint.
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved