
TTA Main Function BMT-Verification of all functions
Feature Flowchart
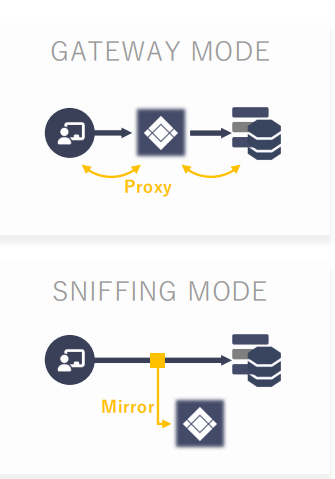
√ Gateway mode(Proxy).
√ Sniffing mode(Mirroring)
Supporting Spec
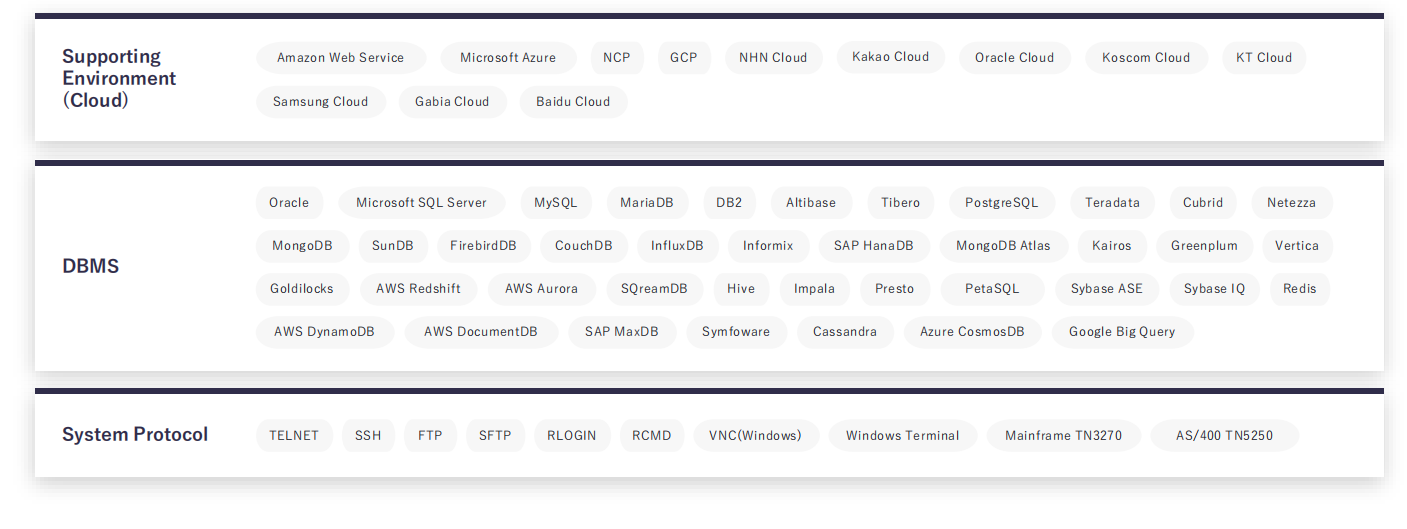
√ Most DBMS supported in Korea
√ PPC Architecture,Supports special protocols such as AS/400-TN5250(Korea's only)
Compliance
Protection Act,external audits,and ISMS-P certification
√ Standardized solutions for the Financial Supervisory Service and major accounting firms
Compliance Applicable in South Korea

Common Applicable Compliance

|
Functional Classification |
Required Function
|
Applicable laws (Korean standards) |
Support Module
|
|
Authority Management |
-Granting least privilege -Authority settings for each user/role -Logging when Granting, changing, and deleting |
- Article 29 of the Personal Information Protection Law, Article 30 of the Enforcement Order -E-Financial Supervision Authority setting for each user/role |
-DB Access Control -System Access Control
|
|
Access Control
|
- IP/MAC-based access control - Access control during specific times - Access blocking for unauthorized users"
|
-Article 30 of the Enforcement Order of the Personal Information Protection Act -Article 28 of the Information and Communication Network Act -Article 25 of the Electronic Financial Supervision Regulations |
-DB Access Control -System Access Control
|
|
Access Record Management
|
- Create access history and store for at least 1-2 years - Prevent tampering with logs - Monitor and alert on abnormal access logs
|
-Article 30 of the Enforcement Order of the Personal Information Protection Act -Article 28 of the Information and Communication Network Act -Article 30 of the Electronic Financial Supervision Regulations
|
-DB Access Control -System Access Control
|
|
User Certification
|
- Create access history and store for at least 1-2 years - Prevent tampering with logs - Monitor and alert on abnormal access logs
|
-Article 30 of the Enforcement Order of the Personal Information Protection Act -Article 28 of the Information and Communication Network Act
|
-DB Access Control -System Access Control
|
|
Electric Ledger Management
|
- Automatically records and saves the contents before and after changes, and records the changes
|
-Article 27 of the Information and Communication Network Act |
-DB Access Control
|
|
Abnormality detection and blocking |
- Detection of abnormal behavior (e.g., excessive privileges, unauthorized IP addresses) - Real-time alerts and automatic blocking
|
-Article 30 of the Information and Communication Network Act
|
-DB Access Control
|
|
Account Creation and Delete Management
|
-Administrator approval when creating, changing, or deleting an account -Account issue, change, and deletion history storage - Abnormal account activity detection
|
-Personal Information Protection Act Enforcement Order Article 30, Items 1 and 3 -Article 28 of the Information and Communication Network Act
|
-Account Management
|
|
PW policy
|
- PW complexity setting - Period change request - Setting to always change initial password |
-Personal Information Protection Act Enforcement Order Article 30, Item 8 -Article 28 of the Information and Communication Network Act
|
-Account Management
|
|
Inactive Account Management |
- Automatically block accounts that have not been accessed for more than 6 months - Automatically delete unnecessary accounts
|
- Article 30, item 8 of the Enforcement Order of the Personal Information Protection Law - Information and Communications Network Law (Notification of the Broadcasting Committee)
|
-Account Management
|
Main Features
DB Access Control
Track and monitor all routes that can access the database,and control unauthorized access and data access.
√Access control /SQL control /masking /auditing features
System Access Control
Supports detailed permission management and policy settings for each user,and prevents security incidents by controlling illegal access and prohibited commands in advance.
√Authority verification/control function/video recording/audit function
4.Audit Feature
Integrated Account Management
Support heterogeneous system-integrated DBMS account management and Access Control Module Linkage
√Security enforcement by unification of integrated account management and account policy
√Improve work efficiency with automated account and password management
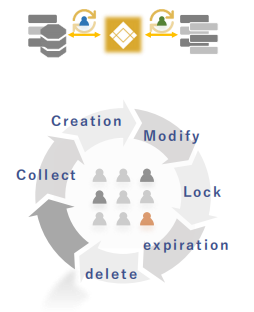
√Automated PW change
√PW policy management
√Heterogeneous System integration Management Policy
√Account security profile management
√Invalid(creation/deletion) Account detection
√Unused Account Management
Solution Features
Own developed DBMS - PetaSQL v3.0 is equipped
√ Efficiency enhancement of System Resource (Conservative Space, Memory, Disk I/O)
√Enhancement of Log retention efficiency/log query rate with data compression technology
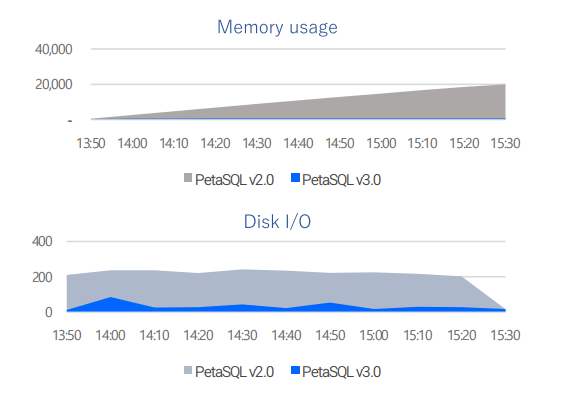
·Lighter (1/10)
Log storage efficiency increased by approximately 1/10 compared to competitors
·Faster
Log search efficiency increased by 400% compared to competitors
·Safer
Audit log encryption and anti-forgery/anti-tampering features
Supports various user OS environments such as Windows, MacOS, Linux, etc. and user portal (WEB)
√Supports System-DBMS One-click auto access function via Client program (* Korea's only)
Advanced masking function applied
√ Supports regular expression for masking (*Korea's only)
Supports Length variable regular masking, String rule masking
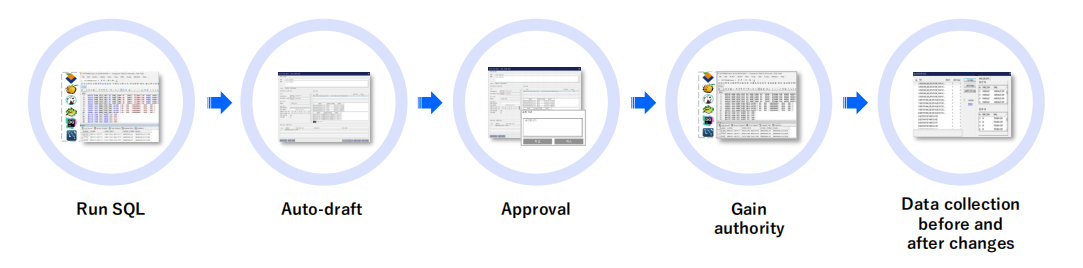
Providing a convenient environment with automated approval flow
√No DBMS access tool limitations(*Korea's only)
√Achieving ledger management function with WV's unique technology
Automatic settlement and ledger management
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved