Cornerstone MFT
Enterprise MFT Server Solution with high availability and failover to eliminate downtime. Advanced automation for improved productivity, SFTP Server for file transfers, and security that exceeds industry standards.
SECURITY
Take advantage of advanced encryption methods, secure protocols, and perimeter security.
SRT supports the latest NSA-approved security standards, so you never have to wait for your MFT vendor to catch up.
Cornerstone offers the most complete security and data protection of any managed file transfer solution. Multi-layer security features keep your data safe at every point in your workflows and compliant with strict regulatory measures.
Security from the Outside
The DMZedge module offers an additional level of security from the outside, detecting and denying server access to any unauthorized users. DMZedge enables you to close inbound ports in your firewall, reducing the risk of network intrusion and enabling the highest level of security for both data storage and transfers.

Your Files are ALWAYS Encrypted
Other MFT solutions allow stored data to be exposed for thousands of processor cycles before it’s encrypted. Cornerstone’s streaming disk encryption module assures that unencrypted versions of your files are never written to disk. Your data is secure at ALL times.
Streaming disk encryption encrypts and writes files as one action. Unencrypted copies are never written to the server, so your data is never exposed — even for a microsecond. When files are requested by users or sent through automated transfers, the decryption process happens automatically. Users don’t go through the cumbersome process of managing encryption keys and decrypting data. The real-time processing makes securing data-at-rest effortless for your end users.

Ransomware Protection
Add WebDrive as the file transfer client in your Cornerstone solution and protect users from ransomware with WebDrive’s Advanced Endpoint Protection feature. This allows you to choose which programs are allowed to open files and ban those that are not, greatly reducing the risk of malware insertion.
WebDrive maps a drive letter to Cornerstone, so users can get to their files easily and without learning a new interface. Users can access Cornerstone files the same way they access files on their desktop. WebDrive reduces the burden of user training and simplifies tech support.
WebDrive also offers two-factor authentication using SafeNet keys.

HIGH AVAILABILITY
Eliminate downtime with failover and load-balancing capabilities.
Load balancing and failover with strong security.
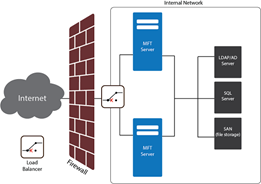
Architecture Built for Protection

Architecture Built for Performance

Skillful Professional Services

Most Cost-Effective HA Solution
International banks, hospitals, and financial institutions rely on Cornerstone for 24/7 operations. Cornerstone’s architecture provides robust fail-over capability, load-balancing for peak processing times, and fast disaster recovery capability.

SECURE COLLABORATION
Bi-directional file sharing and collaboration from every application improves productivity.
Collaborate with customers, partners, and colleagues – without creating security risks

The pace of business requires employees to constantly interact and exchange information. While this fosters unprecedented productivity, it can also come at the expense of security. As users around the country or world interface with your data, there are more opportunities for security risks.
Consumer-focused collaboration services often require syncing data to the local machine. This presents a security risk and wastes local disk resources. Security issues are further complicated by weak access controls and holes in encryption processes. Cornerstone enables sharing and collaboration without locally syncing files. Secure protocols protect transmission of shared files, and controls assure that unauthorized users are never able to gain access to files. Streaming encryption protects data at rest without leaving gaps in security.
Cornerstone’s strong security doesn’t inhibit your users’ ability to be productive. Cumbersome additional steps can drive users to work around security measures by using commercial services for file sharing. Enabling users to work efficiently and in a familiar environment keeps processes under the control and management of your collaboration solution.

COMPLIANCE
Adhere to strict compliance regulations such as HIPAA, GDPR, FIPS 140-2, and PCI compliance.
Scheduled and on-demand compliance reporting and advanced configuration that makes meeting regulatory requirements worry-free
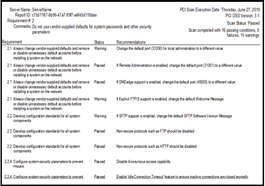
PCI Compliance
Our financial services customers use Cornerstone’s PCI report to assure that all capabilities of the server environment are compliant. Each configuration setting required to meet regulations is evaluated and status is reported. Administrators can schedule this report or run on-demand to validate PCI compliance or to provide audit information.

HIPAA Compliance
For our healthcare customers, Cornerstone offers a variety of ways to protect patient information:

Regulatory Compliance
Cornerstone complies with a variety of security standards:
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved