Oxygen Forensics news vol. 16

We’ve got a lot of exciting Oxygen News to bring you up to date on since our last check-in. Here’s what we’ve been up to!
Screen lock bypass and physical extraction of Sony Android devices
Samsung, Huawei, and Sony devices have always been a challenge for investigators. The manufacturers of these devices use the same chipsets as mid and low-end devices, however, the same extraction approaches cannot be applied to them due to an extra layer of security. Even if a vulnerability is found, it is eventually fixed, and the developed extraction method that required time-consuming research stops working.
Last year we implemented two breakthrough extraction methods that enable screen lock bypass and data decryption from Samsung devices with Exynos chipsets and Huawei devices with Kirin chipsets. However, advanced Qualcomm EDL and MTK bootloader methods that are available in Oxygen Forensic® Detective do not work with Samsung, Huawei, and Sony devices based on Qualcomm or MTK chipsets.
Among high-end device manufacturers, Sony places great importance on their device security. Unlike Samsung and Huawei, Sony devices are not widely used, meaning most forensic software manufacturers are not researching solutions to bypass security. However, our research team has recently succeeded in finding a screen lock bypass solution for Android-operated Sony devices.
Oxygen Forensic® Detective v.13.3 supports data extraction from Sony Xperia XA1, Sony Xperia L1, Sony Xperia L2, and Sony Xperia L3 devices based on MTK chipsets. All these devices run Full-Disk Encryption (FDE), therefore, a physical dump will be encrypted. If Secure Startup is off, Oxygen Forensic® Detective will automatically apply the default password to decrypt the dump. If the Secure Startup was enabled by the user, an investigator can use the built-in brute force module to find the password in the Oxygen Forensic Extractor. The investigator will have an unlimited number of attempts to find the password.
How it works
To extract data from a Sony-Android device, launch Oxygen Forensic Extractor from the main Oxygen Forensic Detective Home screen, and choose “Sony MTK Android Dump”. On the next screen, choose “Sony Android Extraction”.
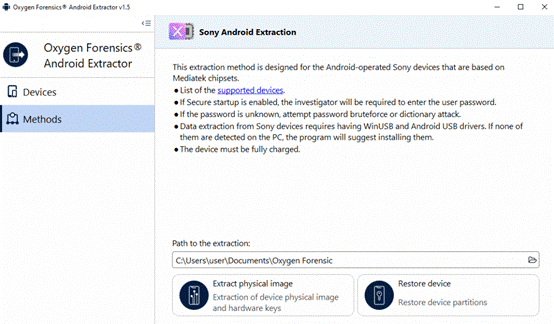
Investigators will see a welcome window with general instructions. The “Extract physical image” option is used to extract device data while the “Restore device” option is used to restore device partitions after the extraction. In most instances, the Oxygen Forensic Extractor will restore partitions automatically once the extraction has completed.
Now let’s extract the Sony Xperia L3 device.
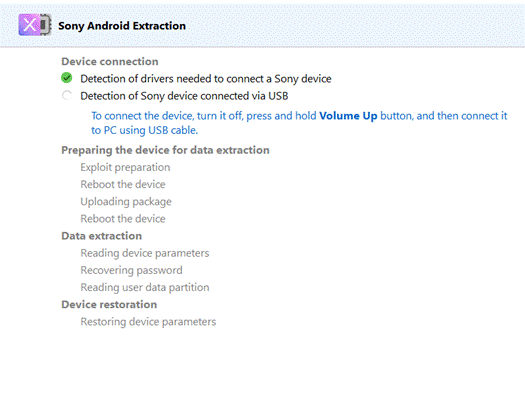
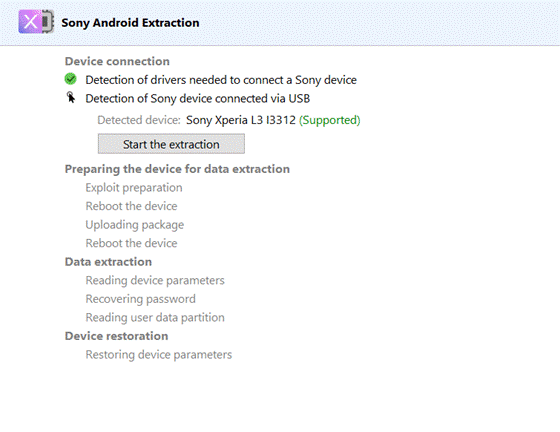
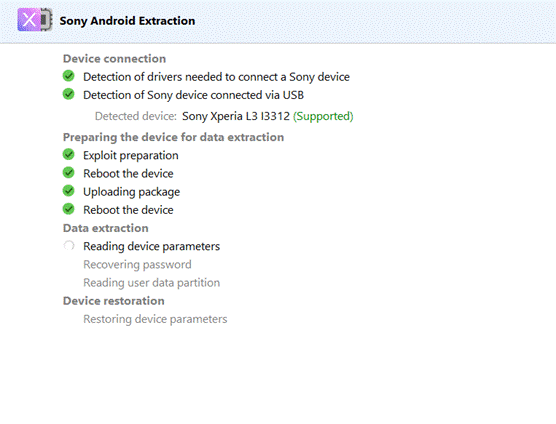
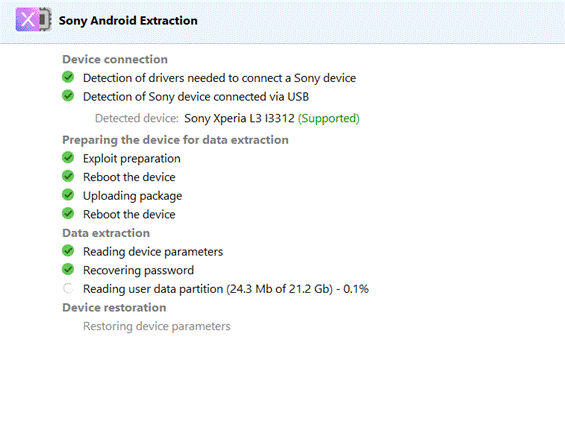
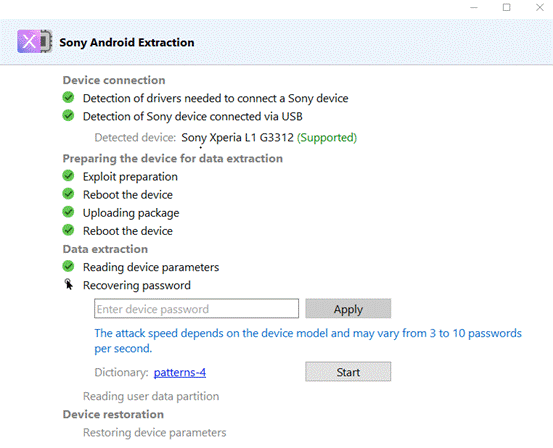
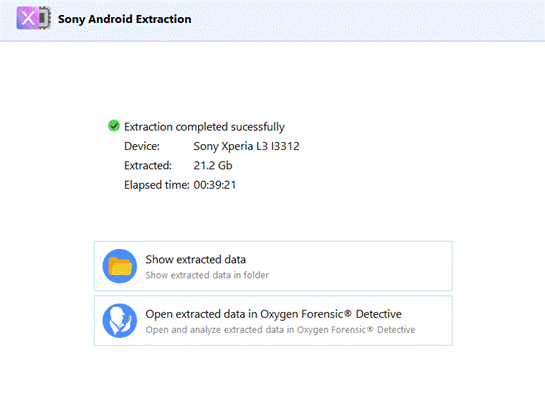
All the screen lock bypass methods available in Oxygen Forensic® Detective offer investigators the opportunity to extract and decrypt evidence at no additional charge. Investigators can also perform these functions on their office computers without asking the forensic software manufacturers for additional paid services. The passcode brute force module is built-in and enables both dump decryption and device unlock after extraction.
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved