Teramind UAM
Activity Monitoring, User Behavior Analytics, Productivity Optimization & Insider Threat Detection in a Single Platform
Prevent Insider Threats with User Activity Monitoring and Behavioral Analytics
Most organizations have cybersecurity measures in place including antivirus, firewall, intrusion detection to protect infrastructure and IT assets. While these are generally good at defending the organization from external threats, they leave a security hole when it comes to employees and other internal users, third party vendors, contractors and privileged administrators who already have access to an organization’s valuable assets and sensitive data.
Whether it is a company’s intellectual property, financial records, customer data, PII, PHI or other sensitive material, it only takes one insider to engage in unwanted behavior and expose an organization to risks. In fact, the majority of the data breaches in recent years involved weak or exploited employee credentials either by malicious or accidental incident (source). This is where User Activity Monitoring (UAM) can help fill the gaps which already includes features like Employee Monitoring, Privileged User Monitoring, Third-Party Monitoring, User and Entity Behavior Analytics (UEBA), Endpoint Security etc. crucial for a holistic insider threat prevention solution.
User activity monitoring is the process of tracking all user activity and behavior, while they are logged into a computer (endpoint). With an employee monitoring solution in place, businesses have the necessary means to keep an eye on their sensitive data, employees and third-party entities so that they can identify and stop the misuse of company data and resources.
Teramind UAM Combines User Activity Monitoring, Behavior Analytics and Productivity Tools in a Single Platform
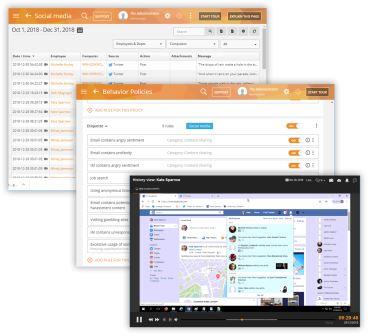
Teramind user activity monitoring goes beyond the basic employee monitoring and tracking functionality and adds intelligent behavior-based analysis to provide actionable insight and automated responses to employee generated threats. It can monitor employees, third-party vendors, contractors, remote and special/privileged users. With its rules and policies, Teramind UAM captures violation incidents as forensic evidence and take action to alert, stop, block and more.
Teramind UAM can also measures employee productivity, conduct risk analysis, prevent unauthorized data exfiltration and keep track of how employees and third-party vendors access company resources while logged in at work. Finally, in case of a data breach or security incident, Teramind provides comprehensive forensic data and session recordings to identify the employees and vendors who have triggered a rule violation along with their activity footprint with pinpoint accuracy.
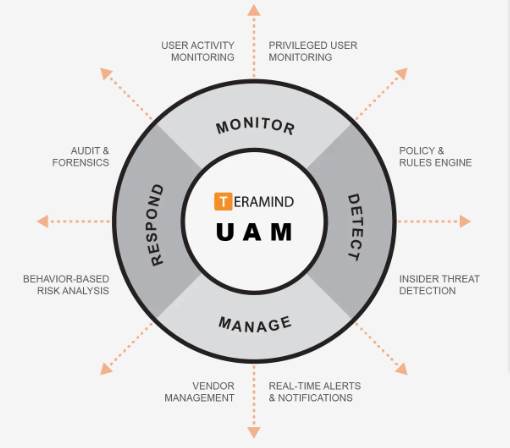
Teramind UAM Features:
Real-Time User Activity Monitoring:
Teramind monitors all employee activity covering 12+ system objects like: web pages, applications, email, console commands, file transfers, instant messaging, social media, keystrokes, clipboard, searches, printing and even on-screen content (OCR) in real-time.
User Behavior Analytics:
Intelligent behavior analysis can detect malicious activity and anomalies that indicate deviation from normal behavioral baseline. Dynamic risk scoring and vulnerability scanning identifies insider activity before they represent a real threat.
Policy and Rules Engine:
Get started right away with hundreds of pre-built rule templates, activity classification lists and data categories. Create your own policies and rules with an intuitive, visual rule editor. Use natural English, regular expressions and sample conditions to easily define your requirements. Create monitoring profiles for individual employees, groups or departments.
Built-In Productivity Optimization: Define which apps and websites you consider productive and get in-depth reports on how your employees utilize them. Identify the laggards or high performers with active vs. idle time analysis. Establish a continuous feedback loop to refine and adjust your organizational workflow through tracking of schedules, projects and employee engagement rate for overall productivity boost.
Audit and Forensics:
Video recording of all employee activity, audio recording, session recording, immutable logs, alerts and optional OCR search are just few examples of Teramind’s powerful audit and forensic capabilities. Together they provide a vast collection of investigative data to locate the source of an insider threat with pinpoint accuracy.
Third Party Vendor Management:
Teramind’s monitoring features cover third party vendors and remote users who have access to your critical systems. This enables you to control vendor management and third-party SLA and decreases the chances of cyber threats.
Compliance Management:
Teramind UAM can be used to create activity and schedule based rules to support several common compliance requirements like: implementing audit trails (GDPR), limiting unauthorized login (ISO 27001), prevent unencrypted file transfers (PCI DSS), reporting, and more.
Teramind Comes with Powerful User & Entity Behavior Analytics Capabilities
Teramind UAM features user and entity behavior analytics (UEBA) capabilities to identify and alert the organization to a wide-range of anomalous behavior and potential threats by either a malicious, inadvertent or compromised employee, user or third-party entity.
Teramind automatically creates a behavioral baseline taking into account a user’s activity (i.e. how many times a user accessed a file), data pattern (file type, source, category etc.), entity role (application, access level, domain etc.) and other attributes (i.e. time of day, schedule, assigned project). Any anomaly or deviation from the normal baseline can then trigger real-time alerts and notification.
Teramind’s Intelligent Policy & Rules Engine then combines this UEBA capability to proactively prevent insider threats while providing the organizations with a clear and complete picture of all user & entity activity, context and forensic evidence in a single solution.
Industry Statistics Prove the Need for Activity Monitoring
Colluding Employees are the Sources of Insider Threats
According to the Community Emergency Response Team, the main reasons for insider caused incidents are collusion from employees and third-parties.
48.3%
Insider-Insider Collusion
16.75%
Insider-Outsider Collusion
Employee Privilege Puts Sensitive Data at Risk
According to a survey of 400,000 member online by Cybersecurity Insiders published on The Insider Threat 2018 report.
37%
Excess Privilege
34%
Increased Amount of Sensitive Data
Employees are a Major Security Concern
Businesses agree employees are their biggest weakness in IT security - according to Kaspersky Lab and B2B International study of over 5,000 businesses.
52%
of Businesses Agree Employees are Biggest Risk
Many Employees Spend Unproductive Time at Work
According to FinancesOnline, 64% of employees use non-work related worksites every day and 85% of employees use their email for personal reasons.
64%
Browse Unproductive Sites
85%
Use Email for Personal Tasks
Teramind User Activity Monitoring Tools

Teramind UAM Delivers Immediate Business Benefits
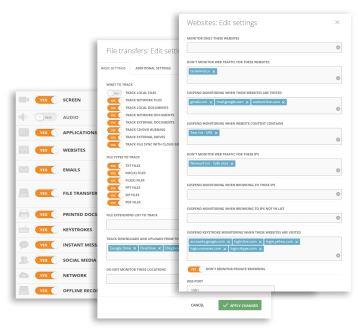
Establish Organization-Wide Visibility and Control
Teramind visually records every action that an employee makes for over 12 objects including screen, apps, websites, files, emails, etc. Each object can be configured to take into consideration what needs to be monitored and measured and who has access to the monitored records. You can control which employees or third-party vendors to monitor, how much you want to monitor, when and for how long. This allows for both instant administrative viewing and respect employee privacy requirements as needed.
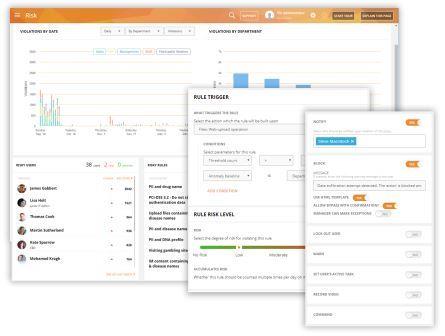
Detect Insider Threats and Vulnerabilities
First, determine what behaviors are high risk i.e. copying files to external drives, using cloud storage to share corporate files, downloading/opening files and attachments from unknown sources etc. Then, apply advanced behavior-based rules to automatically detect when employees violate the rules. Utilize sophisticated anomaly rules to identify employee activity outside the normal behavior. Immediately get notified about harmful employee activity, lock them out from the system or take remote control of their computer before any malicious or fraudulent attempt.
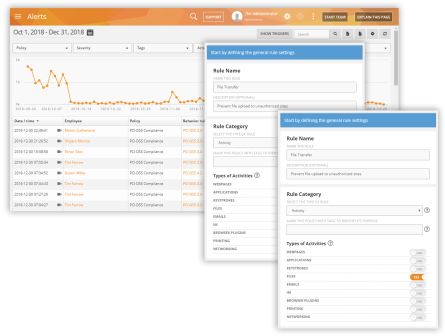
Protect Your Sensitive Data and Resources
Take a look at Teramind DLP if you need a dedicated data loss prevention solution. However, Teramind UAM comes with some useful data protection features too. For example, you can utilize the Activity and Schedule-based rules to prevent external drive usage, detect unusual or unauthorized network login or files transfers. Or, write rules that react to any observable employee activity like blocking an e-mail from being sent outside the company domain, receive instant notification when certain sensitive document gets printed etc. All these features can help minimize information exfiltration and data leaks by malicious or ignorant employees.
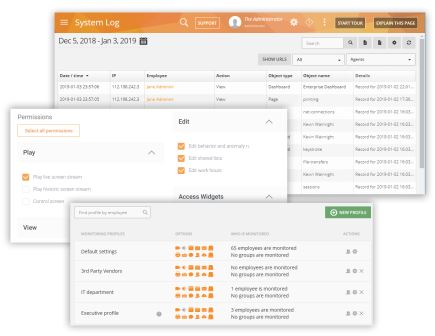
Boost Employee Productivity and Performance
Use the workforce productivity tools to track active vs inactive time, late shifts, long breaks etc. Design etiquette rules to limit unproductive behavior. For example, set a time limit on social media usage or restrict access to gambling sites.
Use intelligent content-based rules to automatically identify clues to customer dissatisfaction (angry sentiments in emails/ customer query in IM chat not answered etc.) and implement processes to provide better service.
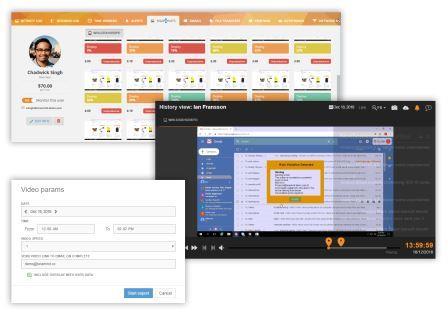
Monitor Privileged Employees and Third-Party Vendors
Teramind allows organizations to stop potential employee-employee or employee-third party collusion attempts. Create profiles for remote, privileged, external vendors and then define what information and system resources each profile can access. Further rules can be set up by behavior policies so that access to sensitive information is segregated by the organization’s security policy, or on a need-to-know basis. Rules can also be created to notify the authorities of any suspicious privileged employee and third-party vendor activity, such as unscheduled and/or unauthorized changes to system configuration, creation of backdoor accounts etc.
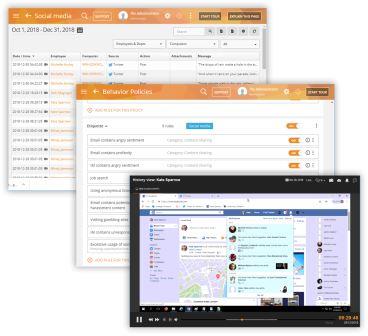
Reduce Organizational Risk and Protect Yourself with Proof
Take action against a malicious employee backed by solid proof. On Teramind, you can view detailed reports for all employees including any security incidents and what steps were taken. Instant snapshots, session recordings and history playback features can be used to view employees desktop for audit and evidence gathering purposes. Video and audio recording can be exported and shared with law enforcement authority.
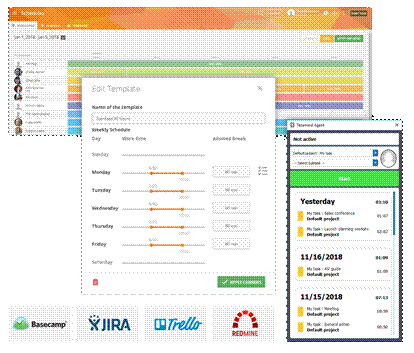
Project Management Benefits
Use the Revealed agent to let employees, contractors or vendors identify and track what projects/tasks they're working on or use the Hidden agent to automatically assign tasks to employees based on their apps/web activity. Use built-in scheduler to track attendance; receive alerts when employees deviate from their scheduled work hours. Timesheet and cost tracking reduce the need for manual invoicing and oversight when working with contractors or remote workers.
Additionally, Teramind has integration support for all your favorite project management tools like JIRA, Trello, BaseCamp, Redmine etc.
HR Management Benefits
HR departments can use Teramind to provide a safe work environment by monitoring internal communication channels for harassment, abuse, resentment. For example, you can create a rule to detect keywords that shows angry sentiment and take proactive measures before it escalates into a conflict. Use etiquette rules to govern acceptable usage policy and code of conduct.
Develop training materials and on-demand feedback system regarding company policy by utilizing the session recording and custom alert messaging features. Same can be used for onboarding new staff or as a guide for an exit interview.
© Copyright 2000-2025 COGITO SOFTWARE CO.,LTD. All rights reserved